The Hacker Webstore

As we visit the challenge page, we can see an online store, which sells products aimed at hacker stereotypes. There are 2 endpoints:
/ for products
/create to create products
/admin to login to the website’s back-end
Since we can create products I tried breaking one of 3 inputs by adding ') to one of them, which returned this very helpful error, which helped understand what was going on.
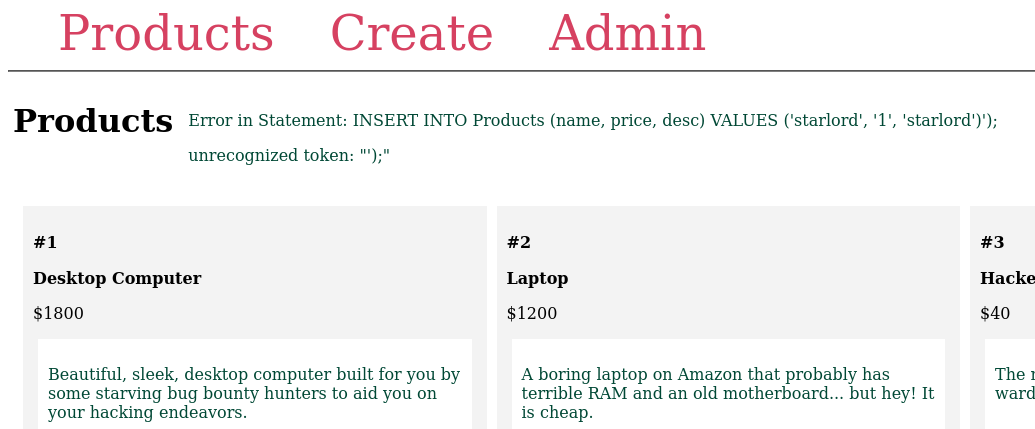
the following payload inserted in the description field did the trick for me:
This will show everything from the table users and comment out the rest of the line.
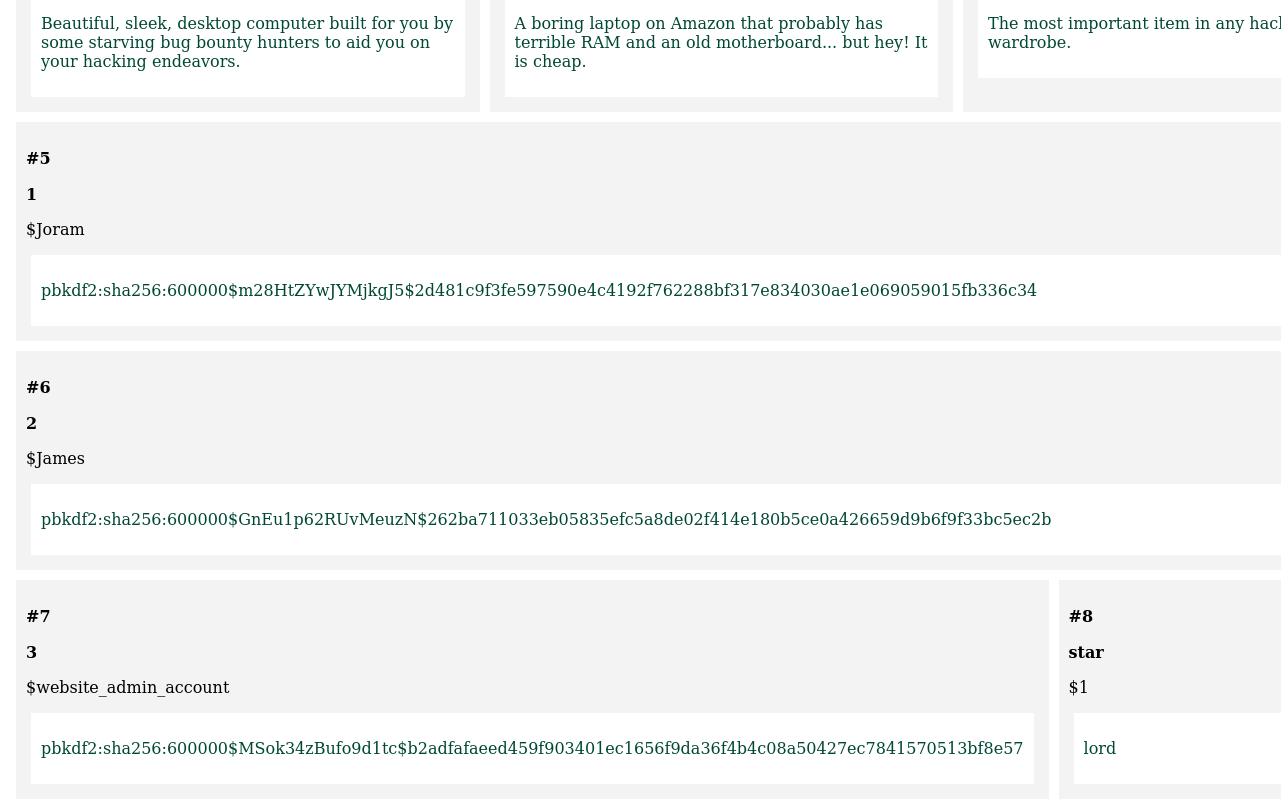
From there it was just a matter of cracking the hashes. But it turned out to be more complicated than usual: As per research, we found out that hashcat and john the ripper, 2 most commonly used tools for cracking hashes, had multiple ways of cracking pbkdf2 sha256 hashes, but none of them had a working function for our specific current hash format. We managed to identify the different parts of the hash thanks to reddit and stack overflow posts which looks like this:
After trying desperately with modes 10900, 10000, 1460, the hashes were not cracking.
Remember, we have 2000 potential passwords in a list given in the challenge description, so even if we have 600k iterations, it shouldn’t take too long.
I ended up making my own decryption tool:
crack.py
I made sure it would print each password to be able to visually confirm progress, as shown below:

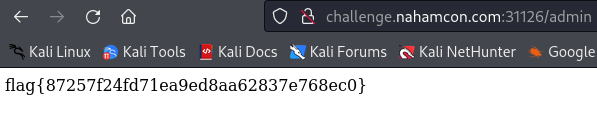
With this, I could then authenticate at /admin and see the flag:
Last updated