Thomas DEVerson
Walkthrough :
command output: {head -n 10 app.py}
from flask import (Flask, flash, redirect, render_template, request, send_from_directory, session, url_for)
from datetime import datetime
app = Flask(__name__)
c = datetime.now()
f = c.strftime("%Y%m%d%H%M")
app.secret_key = f'THE_REYNOLDS_PAMPHLET-{f}'
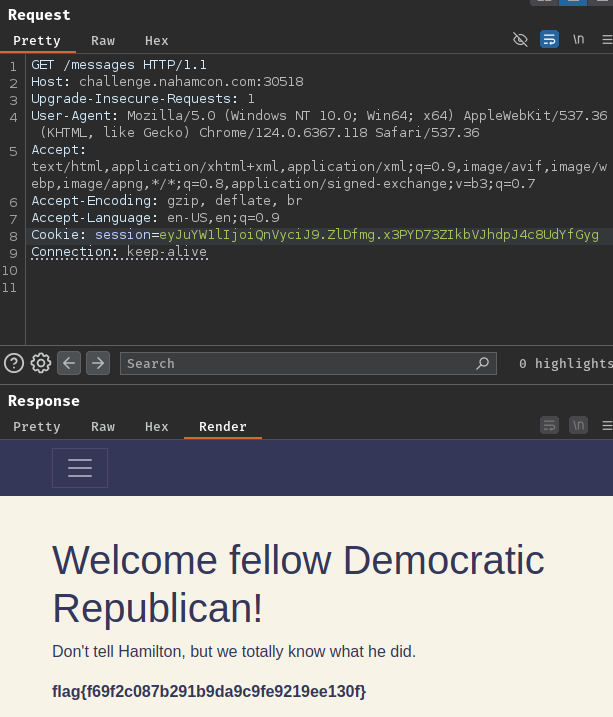
allowed_users = ['Jefferson', 'Madison', 'Burr'] # No Federalists Allowed!!!!
command output: {head -n 10 requirements.txt}
Flask==3.0.3Flag
Last updated